Getting started
SDS for Kubernetes KMS Plugin is a solution that enables the implementation of a Kubernetes Key Management Service (KMS) provider, as described in the Kubernetes documentation.
With SDS for Kubernetes KMS Plugin, sensitive data stored in Kubernetes etcd database is protected by robust at-rest encryption. This solution secures your infrastructure against a wide range of threats, including physical attacks, by protecting your most sensitive data.
It is based on three technologies:
-
Kubernetes KMS provider v2 which encrypts data in etcd using Data Encryption Keys (DEKs).
-
SDS Key Management as a Service (KMaaS) with enabled crypto-api feature: it offers an API for encrypting/decrypting DEKs.
-
Stormshield Software Development Kit (SDK) that provides higher-level and standardized methods to encrypt/decrypt data using DEKs.
The Kubernetes KMS provider v2 uses envelope encryption scheme where data stored in etcd is encrypted with Data Encryption Keys (DEKs) generated from a secret seed combined with random data.
It encrypts data at rest in etcd, including Secrets, ConfigMaps, and custom resources defined in CustomResourceDefinitions. Resources are encrypted on write operations. The encrypted data is stored in etcd prefixed with k8s:enc:kms:v2: to indicate KMS v2 encryption. During startup, the Kubernetes API server performs DecryptRequest procedure calls to fill its watch cache.
Kubernetes KMS provider requires a KMS Plugin to encrypt the seed used to generate the DEKs.
The workflow within the KMS provider is as follows:
-
When the Kubernetes control plane starts, it generates a seed, then sends it to SDS for Kubernetes KMS Plugin via gRPC over Unix sockets.
-
SDS for Kubernetes KMS Plugin generates a DEK and encrypts the seed.
-
The DEK is sent to the KMaaS via HTTPS to be encrypted by a Key Encryption Key (KEK).
-
The encrypted seed and encrypted DEK are stored in etcd. It will be used to generate a DEK each time the Kubernetes API server needs to encrypt data.
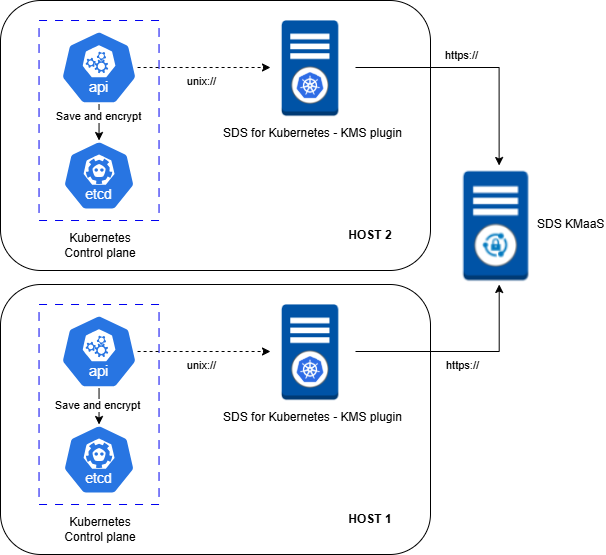
This simplified diagram illustrates a high-availability Kubernetes configuration with two control plane hosts. Each control plane runs a Kubernetes API server that communicates with a local SDS for Kubernetes KMS Plugin via a Unix socket (unix://).
.
NOTE
The use of the solution in any way other than as described in the documentation is not managed.
Alternatively, get in touch with Stormshield Support for clarification.