Managing certificates and certification authorities
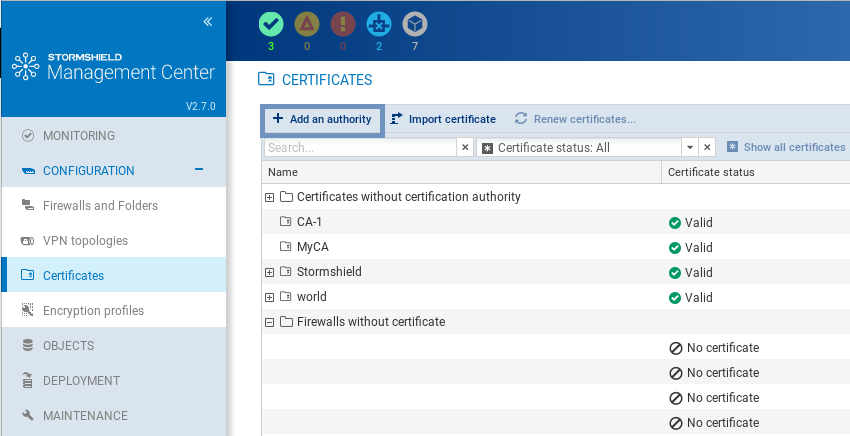
The Configuration > Certificates menu makes it possible to view and manage certification authorities (CAs) and firewall certificates at the same time. From the same panel, you can add, update or delete certificates and certification authorities.
To perform these operations, you need to hold write access privileges on the folders containing the firewalls to which these changes apply. For more information, refer to the section Restricting folder administrators' access privileges.
In the table, authorities, sub-authorities and certificates are presented in a tree structure displaying information on certificates, firewalls and topologies concerned.
- To select the columns to be displayed, scroll over the name of a column and click on the arrow that appears.
- To display the actions that can be performed on authorities and certificates, scroll over the Certificate status column. Action icons will appear.
Firewall certificates can be in X509 or issued via SCEP or EST, and allow different actions to be performed:
| Certification authorities | X509 certificates | SCEP/EST certificates | |
|---|---|---|---|
| Icons when scrolling over the line |

|

|

|
| Possible actions |
The following characters are not supported in certificate names:
| , | < and > |
| + | # |
| = | ; |
| " | double space |
Refer to the procedures below for more information on each of these actions.
The SMC server does not allow the use of certification authorities with unknown issuers. Therefore, when importing a certification authority, its entire chain of trust must be imported.
To import a chain of trust, import the certificates of the root certification authority and the various sub-authorities individually, starting with the certification authority of the highest level. You can also import all of them at one go by providing a "bundle" file.
Whenever you add a certification authority, the SMC server will verify its chain of trust.
- In Configuration > Certificates, click on Add an authority.
- Select a file in .pem, .cer, .crt or .der format and click on Add.
- Add the addresses of the distribution point(s) for the certificate revocation list (CRL). For more information, refer to the section Configuring a policy-based mesh topology.
- If you renew firewall certificates via SCEP or EST, associate an SCEP or EST server with the certification authority in the Certificate renewal tab.
- After the authority has been declared, you can change it or check its usage by scrolling over the name of the authority in the table to display the action icons in the Certificate status column.
You can also add a new authority during the configuration of a VPN topology, during the selection of the authentication method, by clicking on Add an authority.
Whenever you update a certification authority, the name, comments and list of certificate revocation list distribution points, if there is one, will be kept.
The public key must be the same as the one for the previous authority.
- To update a certification authority, scroll over the name of the certification authority and click on the
 icon in the Certificate status column.
icon in the Certificate status column.
Whenever you delete a certification authority, all authorities depending on it will also be deleted. If any of the intermediate authorities are used in a VPN topology, you will not be able to delete them.
- To delete a certification authority, scroll over the name of the certification authority and click on the
 icon in the Certificate status column.
icon in the Certificate status column.
X509 certificates can be imported via the Firewall column in the table, as well as from other panels in the administration interface.
To import or declare a certificate, refer to the section Importing or declaring a certificate for a firewall.
After the certificate has been imported or declared, you can check its usage or delete it by scrolling over its line in the table to display the action icons in the Certificate status column.
You cannot delete it if it is in use in a VPN topology.
If you have imported several X509 certificates for a firewall, to find out which certificate is used by default in VPN topologies, refer to the section Importing or declaring a certificate for a firewall.
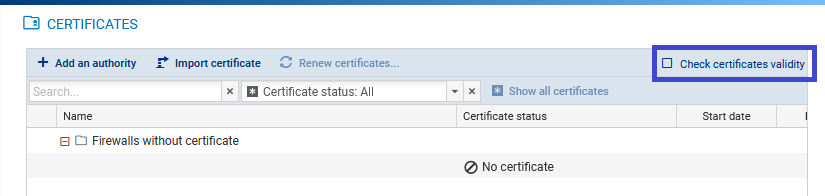
You can configure SNS firewalls to look up the CRL (certificate revocation list) when they need to verify the validity of the certificates that VPN tunnel peers use.
This verification is mandatory in DR (Diffusion Restreinte) mode.
- Select Check certificate validity at the top right side to make the presence of a valid CRL mandatory, and therefore detect revoked certificates. In the absence of a valid CRL, or if the peer presents a revoked certificate, the VPN tunnel cannot be set up. This option is equivalent to the CRLRequired parameter on SNS firewalls.
- For each certificate, configure if necessary the local IP address to use for the verification and frequency of verifications. To do so:
- Show the Local IP address for CRL verification and/or CRL verification frequency columns by scrolling over the name of a column and clicking on the arrow, then on Columns.
- Select a certificate.
- In the Local IP address for CRL verification column, select the desired address. Any can be used by default.
- In the CRL verification frequency column, enter the number of seconds between each verification. The default frequency is 21600 seconds, or 6 hours.
- To update an X509 certificate that has expired or is about to expire, scroll over the line of the certificate in the table and click on the
 icon in the Certificate status column.
icon in the Certificate status column.
The new certificate must have the same subject field as the previous certificate.
To ensure the successful renewal of SCEP or EST certificates, the address of the SCEP or EST server must be entered in the Certificate renewal tab of the certification authority that issued the certificates, as shown in the section Adding a certification authority or chain of trust.
If necessary, you can choose the SNS firewall address that must be used for the renewal of the certificate.
The following conditions must be met in order to renew certificates:
- SNS firewalls must be at least in version 3.9.0 for SCEP and at least 3.10 or 4.1 for EST,
- the SNS firewalls must be connected.
To choose a specific address for a certificate renewal:
- Show the Local IP address for renewal column by scrolling over the name of a column and clicking on the arrow, then on Columns.
- Click in the column of a certificate and select the desired address of the SNS firewall from the drop-down list.
To renew certificates:
- Click on Renew certificates... at the top of the table,
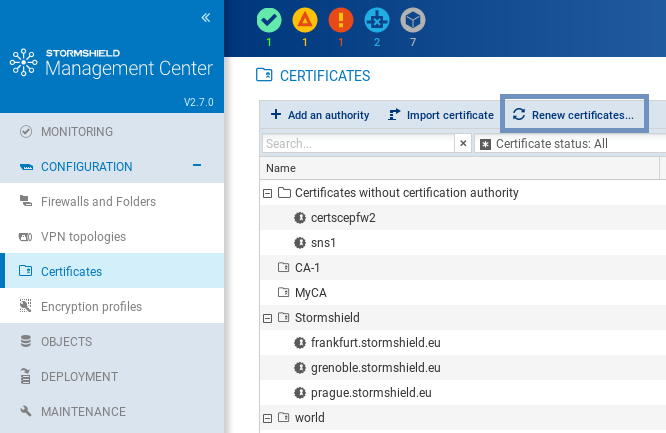
- Select the certificates to be renewed,
- Confirm the renewal of the certificates at the bottom of the table. If an error occurs, refer to the server logs for more information.
TIP
To renew a single certificate, scroll over its line in the table and click on  in the Certificate status column.
in the Certificate status column.
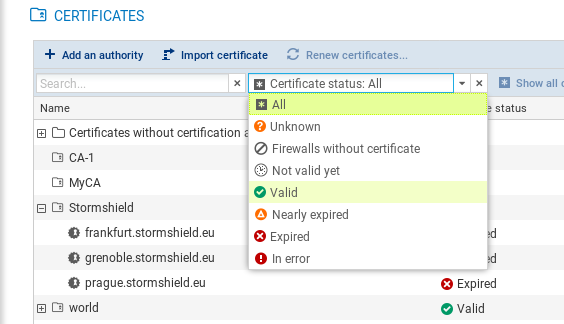
The filter above the table allows you to display certification authorities and certificates according to their status.
To view the entire certificate tree, click on Show all certificates.
The Unknown status applies only to certificates obtained via SCEP or EST. SCEP or EST certificates may be Unknown if the SMC server does not yet know the certificate. This happens when the SCEP or EST server cannot be reached or the firewall has not connected since the certificate was created.
The Nearly expired status appears by default 30 before the expiry of the certificate. To configure the warning when a certificate is close to expiry, refer to the section Configuring the warning for an imminent certificate expiry.
IMPORTANT
As the SMC server does not manage certificate revocation, revoked certificates will appear as "Valid".