Allowing administrators to connect via an LDAP or Radius server
The SMC server can be connected to an LDAP and/or Radius server to authorize the company’s users to manage a pool of firewalls.
This type of authentication is designed to operate with LDAP servers such as Active Directory on Microsoft Windows Server 2016 and 2019 or OpenLDAP in at least version 2.5, and Radius servers on Microsoft Windows Server 2016 and 2019.
When the super administrator tries to connect, the SMC server looks for the ID and password from its local user database.
When an ordinary administrator tries to connect, the SMC server looks for the ID and password on the Radius server first, and then on the LDAP server if it does not find this information, then in its local user database.
Authentication via LDAP or Radius server is configured in the SMC web administration interface.
To authorize administrators to connect to the SMC server via an LDAP or Radius server, follow the three steps below:
- Configure the connection to the LDAP or Radius server,
- Test the connection to the server,
- Authorize users and define their access privileges.
To configure and enable the connection to an LDAP server:
- Go to Maintenance > SMC Server > Administrators, and click on Edit local authentication settings,
- In the LDAP tab, select LDAP authentication enabled.
- Fill in the following fields:
Field Description Server type Active Directory or OpenLDAP server Host IP address or FQDN of the main LDAP server.
If the server’s FQDN is used, the DNS service must be configured beforehand.
If you use the SSL protocol to secure the connection to the LDAP server, the host name must be the same as the common name (CN) of the LDAP server’s certificate.
Backup host Optional - IP address or FQDN of the backup LDAP server.
If the server’s FQDN is used, the DNS service must be configured beforehand.
Only this parameter is required for the backup LDAP server, as the other parameters belong to the main server.
Port Port number to access the LDAP server: if SSL is enabled, 636 by default; otherwise, 389. Base DN Base DN that enables access to the LDAP server and uses the following format: dc=sub,dc=domain,dc=com. The Base DN can also refer to a more specific location in the Active Directory, e.g., an organizational unit: ou=unit,dc=domain,dc=com ID
This field appears if an Active Directory server is used. Refers to the ID of the administrator with which a request can be submitted to the Active Directory LDAP server.
Administrator DN This field appears if an OpenLDAP server is used.
Refers to the DN of the administrator with which a request can be submitted to the OpenLDAP LDAP server.
Password Password to connect to the LDAP server Encrypt with SSL If the option is enabled, the connection to the LDAP server is secured via SSL/TLS protocols.
When SSL is enabled, the default port changes.
If SSL is enabled, the SMC server does not verify the certification authority that signed the LDAP server’s certificate by default.Check identity of the LDAP server CA This option makes it possible to verify the certification authority that signed the LDAP server’s certificate, when SSL is enabled. Provide the CA’s certificate in the field below. Certificate In this field, the certificate of the certification authority that signed the certificate that the LDAP server used for the secure SSL connection can be forwarded to the SMC server.
To configure and enable the connection to a Radius server:
- Go to Maintenance > SMC Server > Administrators, and click on Edit local authentication settings,

- In the Radius tab, select Radius authentication enabled.
- Fill in the following fields:
Field Description Host IP address or FQDN of the Radius server.
If the server’s FQDN is used, the DNS service must be configured beforehand.Port Port number to access the Radius server: 1812 by default Pre-shared key Secret key shared to enable authentication on the server
Backup server - Optional Host IP address or FQDN of the backup Radius server.
If the server’s FQDN is used, the DNS service must be configured beforehand.
Port Port number to access the Radius server: 1812 by default Pre-shared key Secret key shared to enable authentication on the server
To test the connection to LDAP or Radius servers, use the ldapsearch or radtest tools available in command line on the SMC server.
Testing the connection to LDAP servers
Use the following parameters with the ldapsearch command to test the connection to an LDAP server and perform a search in the directory:
| Parameter | Description |
|---|---|
| -h | IP address or FQDN of the LDAP server |
| -p | LDAP server port. If nothing is entered, port 389 will be used by default. |
| -D |
Unique name used to authenticate on the server. This name must match a specific entry in the directory and must be allowed to perform searches in the directory. |
| -W | If a term is entered, an authentication password will be requested before launching the search |
| -b | baseDN used for the search in the directory |
EXAMPLE
ldapsearch -h 1.2.3.4 -p 567 -D "CN=Administrator,CN=Users,DC=mydomain,DC=com" -W -b "CN=Users,DC=mydomain,DC=com"
Testing the connection to Radius servers
Use the radtest command to check whether a user exists on the Radius server.
EXAMPLE
radtest <user-id> <user-password> <Radius-server-ip> <Radius-server-port> <pre-shared-key> 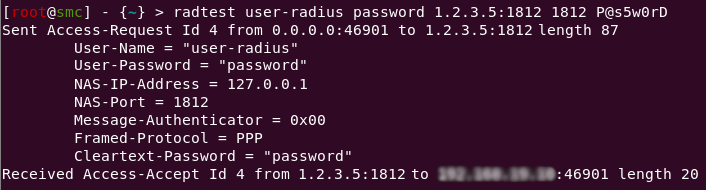
To allow LDAP or Radius users to authenticate on the SMC server, the super administrator must add them to the list of administrators in the web administration interface.
Users can belong to LDAP or Radius groups.
NOTE
To enable users belonging to an OpenLDAP group to authenticate on SMC, you must configure the memberOf attribute on the OpenLDAP server. For more information, refer to the section Changing the default LDAP attributes used by SMC.
In the Maintenance > SMC Server > Administrators menu in the web administration interface, access privileges can be assigned to each user or user group.
To add a single user, refer to Managing administrators in the web interface.
To add an LDAP or Radius user group:
-
In the Administrators menu, click on Add an LDAP/Radius group.
-
Fill in the fields and select the access privileges that group members require.
-
For LDAP authentication servers, indicate the group’s DN,
-
For Radius authentication servers, indicate the group’s ID.
-
If an administrator has a personal account in his/her name, and is also a member of one or several groups, the privileges that apply will be those assigned to the personal account.
NOTE
The IDs of users authenticated via the LDAP directory must not contain spaces in order to be able to connect to the SMC server.
In the SMC Server window > Administrators > Add an administrator, the ID and LDAP DN fields correspond to the following LDAP attributes by default:
| ID |
|
| LDAP DN |
|
SMC also relies on the memberOf attribute - to be configured manually on the LDAP server - to search for groups in which users belong.
The following environment variables make it possible to change these three attributes:
-
FWADMIN_LDAP_FIELD_NAME_LOGIN
-
FWADMIN_LDAP_FIELD_NAME_DN
-
FWADMIN_LDAP_FIELD_NAME_MEMBEROF
To change their values:
- Log in to the SMC server via the console of your hypervisor or in SSH.
- In the file /data/config/fwadmin-env.conf.local, change the values of these environment variables:
- Restart the server with the command
nrestart fwadmin-server.