Interconnecting networks with overlapping address ranges
In this case, neither of the private networks can use their real IP addresses through the tunnel as the peers would assume that they belong to the same network and would therefore attempt to contact each other directly on this local network instead of going through the IPsec tunnel.
The strategy to adopt would therefore be to:
- Hide the real IP addresses of the hosts on Network A from the hosts on Network B and vice versa,
- Indicate to the hosts on Network A that Network B uses a different address range,
- Restore the real destinations when leaving the tunnel in order to transport packets to the real IP addresses of the hosts on both networks.
This would require modifying the source IP address before sending the packets through the IPsec tunnel, and restoring the real destination IP address in the packets coming from the tunnel on both of the sites to be linked.
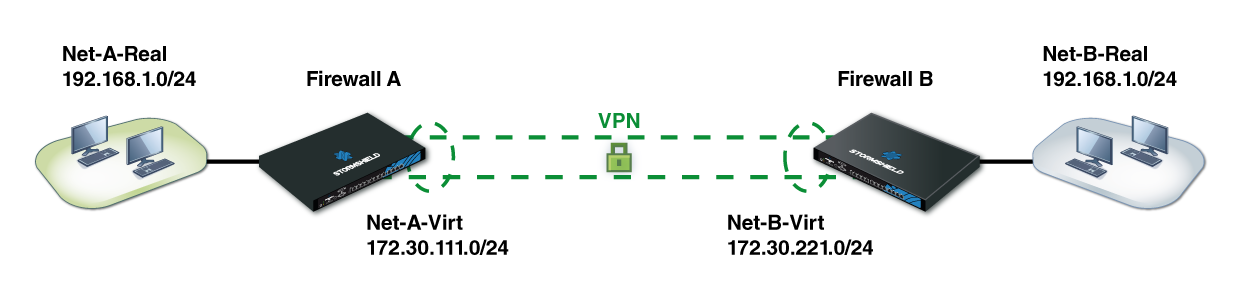
In this example, Net-A-Real and Net-B-Real are in the same address range.
We have defined as follows:
- Net-A-Virt to represent Network A as Network B will see it,
- Net-B-Virt to represent Network B as Network A will see it.
The IPsec policy will only know the “virtual” IP address ranges (-virt), as source addresses would have been translated before going into the IPsec tunnel (before encryption) and destination addresses would be translated after having gone through the tunnel (after decryption of the packet that came from the tunnel).