Attribute-Based Access Control (ABAC)
What is ABAC?
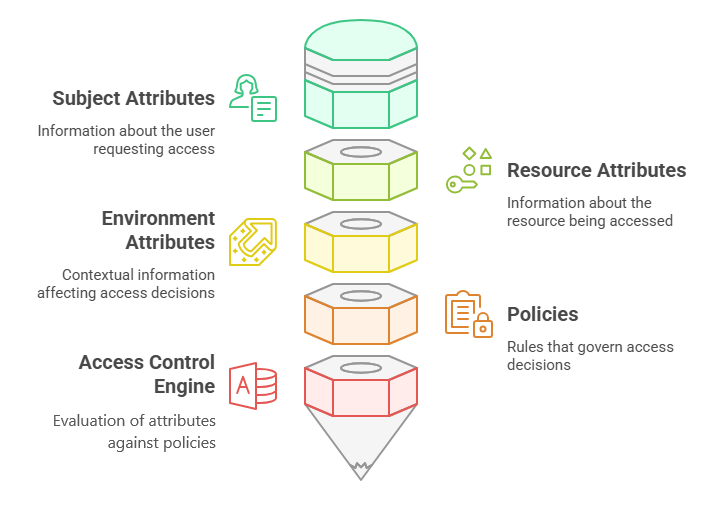
Attribute-Based Access Control (ABAC) is an access control model that grants or denies access to resources based on a set of attributes associated with the user, the resource, and the environment. These attributes can be the user identity, role, department, job function, location, time of day, and more.
How ABAC works?
Here's a high-level overview of the ABAC process:
- Attribute collection: The system collects attributes from various sources, such as user directories, databases, and environmental sensors.
- Policy evaluation: The system evaluates the collected attributes against a set of policies defined by the organization.
- Access decision: Based on the policy evaluation, the system grants or denies access to the requested resource.
How ABAC work in Stormshield Encryption Platform?
During encryption, attributes are attached to the data. Prior to decryption, the attributes along with additional information (e.g. JWT details, as specified in the KMaaS documentation) are sent to a policy server (OPA) for authorization evaluation. For more information on the OPA policy server configuration and use, refer to sections 7.2.2.2 and 10 of the KMaaS documentation. If the access is granted, the encrypted Data Encryption Key (DEK) is transmitted to the KMaaS service for decryption. The OPA policies must be configured and implemented according to your specific requirements. For more information on writing OPA rules in the ABAC process, refer to section 10.6 of the KMaaS documentation.
